Late afternoon links
AviationBlogsCassieChicagoElection 2028PersonalSecuritySoftwareTrumpUrban planningWinterWork
I haven't had a chance to work on the comments problem, because, you see, I have another job. I've also had a plumber and a carpet cleaner here today, traumatizing poor Cassie who couldn't show them her blanket because she got shoved into a different room. She's now on her bed in my office rather than on one of the couches downstairs. I expect she'll get over the soul-crushing exile she experienced for nearly an hour today.
If only she knew what the rest of the world was like:
- Ezra Klein says the OAFPOTUS "has overwhelmed himself," blowing way past the limits of the administration's miniscule competence: "That is why most White Houses pay such close attention to policy processes and chain of command: These are all ways of filtering the torrent of information and decisions in order to conserve the focus and attention of the president and his top aides." Ruth Ben-Ghiat told you so.
- In case you need it, Paul Krugman has a refresher on the Federal Reserve.
- Matt Yglesias doesn't see a lot of difference between California Governor Gavin Newsom and former Vice President Kamala Harris. (Personally, I think Newsom will be a great vice president to JB Pritzker.)
- James Fallows explains what we know and still don't know about the helicopter-jet collision over Washington last year.
- The City of Chicago has released 25 finalists for the "You Name a Snowplow" contest, with "Abolish ICE" taking the lead with 80% of the nominations. (My favorite is "Daniel Brrrnham.")
Finally, be careful which LLMs you use to help with your coding. KOI has discovered that MaliciousCorgi extensions send everything you type (and then some) back to unknown endpoints China. I'll stick with Claude and ChatGPT on Copilot for now.
Pinned posts
- About this Blog (v5.0) (1 week)
- Brews and Choos project (1 month)
- Chicago sunrises, 2026 (1 month)
- Inner Drive Technology's computer history (2 years)
- Logical fallacies (6 years)
- Other people's writing (5 years)
- Parker Braverman, 2006-2020 (5 years)
- Style sheet (7 months)
- Where I get my corn-pone (1 year)
I've just discovered comments aren't working for anonymous users. They appear to work, and the logs say they worked, but they're not saving to the comment index.
I'll get this fixed by tomorrow. Apologies if you've tried to leave a comment recently. If you log in with a Microsoft account, however, you will have no problem commenting.
Happy February!
Yesterday got up to -3.2°C, the warmest we've had since 1am a week ago Thursday. Officially at O'Hare the temperature hit -3.9°C. Reading the forecast is excruciating: -3°C today, -2°C tomorrow, the same Tuesday and Wednesday, with the possibility of just touching freezing on Thursday afternoon.
Cassie got an hour and 20 minutes of walks yesterday, though, so at least she and I are no longer climbing the walls. We're about to go out again as the sun will make the -3.6°C feel almost tropical. First, though: groceries. Nothing can slow this swinger down today!
Cassie and I just finished a 41-minute walk through the neighborhood, bringing her total walkies over an hour for the first time in a week and a half. As I mentioned yesterday, we've both gone a bit stir-crazy without the exercise.
While it is a tiny bit warmer today, it's still below freezing. But now it's close enough to freezing that the tons of salt have started working again so tonight someone will get an overdue bath.
At least I'm now over 310,000 steps for January, which means I still have gotten at least 10,000 steps per day on average every calendar month since I started keeping track in October 2014. It's a small victory.
Friday afternoon news roundup
CrimeEconomicsImmigrationLawPolicePoliticsTrumpUS PoliticsWinterWorld Politics
The sun just came out, reminding me that gray skies don't last forever. Neither will all this crap:
- The OAFPOTUS swapping out the head of the Lollipop Guild1 for the guy who took $50,000 from an FBI agent in a bribery sting doesn't change anything in Minnesota.
- Molly White asks, where are all the freedom-loving crypto bosses now? Right: they're bankrolling the administration and the Congress who are causing all this shit. Because right-wing governments are always, always about the grift.
- Nobel-winning economist Paul Krugman explains exactly how the OAFPOTUS's pick for Federal Reserve Chair will likely be "the least influential...ever."
- Jeff Maurer reminds the sane among us that it doesn't matter whether victims are "good" or "bad".
- Julia Ioffe introduces us to "the 'MAGA Barbie' redecorating the State Department."
- Josh Marshall draws a straight line between billionaires demanding privacy for things that everyone else has to declare publicly and ICE doing the same thing. Hint: neither group wants accountability for their actions.
Well, I guess that's it. And the skies are cloudy again.
-
You just can't unsee it once you've seen it...↩
Cassie and I took a 2.88 km walk at lunchtime today, which turned out to be the longest walk we've taken since January 11th (6.28 km). Why? Because for the first time in over a week, the temperature got above -6°C. No kidding: it hasn't been this warm since 2:16 am last Thursday.
In fairness, we took the same route as a walk on January 13th, which was 60 meters and 4 seconds shorter only because of where I started the workout on my Garmin. Of course, that walk was 14 degrees warmer than today's.
After two weeks of below-freezing weather, I'm done. The National Weather Service doesn't have above-freezing temperatures in the 5-day forecast, but Weather Underground has us above freezing a week from today.
Cassie has a full double coat, which has thickened considerably in the last few weeks (woe to my vacuum cleaner in February). So my rule of thumb is that above -8°C (18°F) we can stay outside for 30-35 minutes, and above -5°C (23°F) until one of us gets cold. Above freezing there's no limit; her fur is that thick. Which is why I really, really want a thaw. It's supposed to be -4°C tomorrow, which is warm enough to walk to the dog park, as long as we pop into Burning Bush Brewing to warm up after.
Also, because we haven't been able to walk very much, I just had seven days in a row without making my 10,000 step goal. I got only 58,132 steps last Friday through yesterday. Today I'm already over 8,000, so I am pretty sure I'll get there, just as I'm pretty sure I'll be over 310,000 for January as I have 300,847 so far. But this will be my worst month for steps ever. (I got 305,385 steps in February 2021, but that's still 10,906 per day.)
Lack of exercise has made me irritable and made Cassie barky. (She may be irritable too, but she's such a sweet dog it's hard to tell.) The mild warm-up over the next week will, I hope, help.
The temperature has just barely gotten above -10°C (14°F) today, with a possibility of more tolerable temperatures by Saturday. Still, the official NWS forecast has us below freezing as far out as it goes; some commercial forecasts hint at, but do not commit to, an above-freezing reading sometime next Friday. We've already had 13 days below freezing; that would make it 21.
Our local television station says it's the coldest back half of January in 63 years. Plus, "the entire eastern two thirds of the U.S. remains firmly in the deep freeze as highs were some 15° to 20° [Fahrenheit, 8° to 12°C] below normal." However, our local PBS station posted a graphic from the National Weather Service showing the possibility of above-freezing temperatures on February 8th, 23 days into the freeze. That's still not as bad as the freeze from 28 December 1976 to 8 February 1977 (43 days), or the runner-up from 15 January to 16 February 1985 (33 days) that also saw the coldest temperature ever recorded here, -33°C (-27°F).
It is sunny, though. I'll give it that. It might not be warm enough to walk Cassie home from day care, however.
Only 29 days of winter left.
I just pushed a minor update to the Daily Parker's blog engine, the thing that you're looking at right now. I fixed a couple of performance bottlenecks, so I hope the experience is a bit faster. (You can always check out the release notes for a summary of what I've done.)
I also checked the app metrics in Azure. Since this runs on Azure hardware, I can see a lot of data about how well it's running, which is how I kept track of the painful senescence of its previous incarnation. Unlike every day with the BlogEngine.NET implementation that I retired two weeks ago, this software has no glaring failures or crashes so far. So while I got it to speed up a little bit in a few places this week, it's not like before when it could take 30-40 seconds for a post to load if more than 100 people tried to read the blog at the same time.
Next up: improvements to the Search by Tag feature, followed by the new privacy levels I've planned for years. That will segue into the first "life event" data type: my reading list. Logged-in users will be able to see most of it; I'll be able to see all of it, plus private notes. I'm starting with that in order to limit the blast radius of any data leaks if I don't get the security right.
Stay tuned.
On 28 January 1986, 40 years ago today, the Space Shuttle Challenger exploded 73 seconds after launch from Kennedy Space Center in Cape Canaveral, Fla. Six astronauts and a teacher from New Hampshire died when the crew cabin of the orbiter impacted the Atlantic Ocean more than three minutes later; most of them were likely conscious and aware at the time.
The Rogers Commission Report on the disaster concluded that Morton Thiokol managers Jerry Mason, Joe Kilminster, and Robert Lund had overruled their engineers, particularly Bob Eberling, under pressure from Lawrence Mulloy and George Hardy at NASA.
Physicist Richard Feynman revealed the systemic failures at both organizations, in particular NASA's habit of determining what the probability of disaster ought to be, and then working backward to the data they actually had, rather than determining the probability from the data. NASA claimed that the probability of a shuttle disaster was 1 in 100,000; the actual probability turned out to be 1 in 67.5 over the life of the program. I am not aware of any other vehicle ever produced that killed its occupants 1.4% of the time and stayed in service for 20 years.
In unrelated news, NPR revealed this morning that the Department of Energy has secretly loosened nuclear safety regulations to encourage development of the next-generation of reactors. According to NPR,
The orders slash hundreds of pages of requirements for security at the reactors. They also loosen protections for groundwater and the environment and eliminate at least one key safety role. The new orders cut back on requirements for keeping records, and they raise the amount of radiation a worker can be exposed to before an official accident investigation is triggered.
The new orders strip out some guiding principles of nuclear safety, notably a concept known as "As Low As Reasonably Achievable" (ALARA), which requires nuclear reactor operators to keep levels of radiation exposure below the legal limit whenever they can. The ALARA standard has been in use for decades at both the Department of Energy and the Nuclear Regulatory Commission.
Removing the standard means that new reactors could be constructed with less concrete shielding, and workers could work longer shifts, potentially receiving higher doses of radiation, according to Tison Campbell, a partner at K&L Gates who previously worked as a lawyer at the Nuclear Regulatory Commission.
Any connection with the Challenger disaster is purely coincidental, except for the part about how both occurred in the second terms of Republican presidents obsessed with corporate profitability at the expense of safety.
On January 27th, we still have 5 weeks until spring officially begins. The forecast doesn't predict any above-freezing temperatures as far as it can see, and we've already had 10 days below freezing in this seemingly endless cold snap.
But also today, the sun sets at 5pm for the first time in 88 days. In only 24 days it sets after 5:30pm, and just 16 days after that, we change the clocks and get a 6:50pm sunset. That's when it will feel like spring.
Another bit of news that warmed my heart today: Customs and Border Patrol "commander at large" Greg Bovino has been sent out to pasture and will retire "soon" according to Dept of Homeland Security officials, which suggests that even if the OAFPOTUS doesn't think Bovino and his goons did anything wrong when they murdered two US citizens in cold blood, someone in the administration can read a poll. There's also a rumor going around that DHS Secretary Kristi "Puppy Killer" Noem has been shoved aside and may soon resign.
One more tidbit that indirectly implicates the OAFPOTUS and Reichsführer-ICE Stephen Miller: the US Census Bureau announced this morning that population growth in the US has slowed dramatically because—wait for it—international migration has fallen by 54% in just one year.
So, things are looking just a bit brighter. Things will get worse, of course, but only temporarily.
Oh, look, the temperature is going up! It's almost all the way to -15°C (5°F).
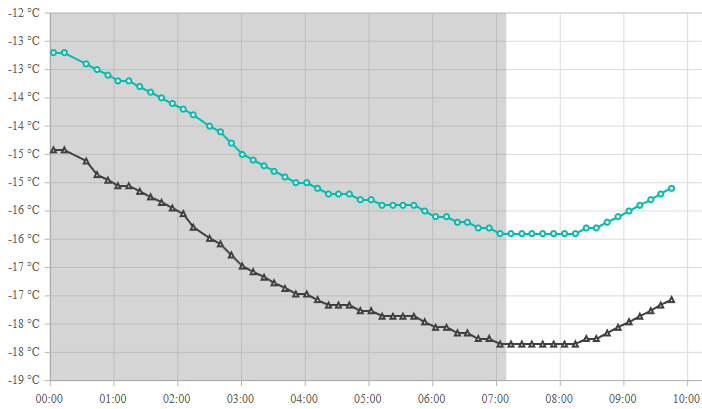
And yet, I've decided not to take my lunch on the patio this afternoon:

Now that the Calendar feature works, I spent an hour today writing a utility to count all the public blog posts by month, and to give me a cumulative count. It turns out, most of my posts exhorting big milestones, like the 5,000th or, more recently, the 9,000th, were off by a few weeks.
Rather than sometime next week as I had thought, I actually published the 10,000th post of the modern era (i.e., since 13 November 2005), on December 26th. The 10,000th post overall was this one from July 10th, not the one on August 8th as previously believed1.
This, therefore, is the 10,248th Daily Parker post since braverman.org added proto-blogging features in July 1997, and the 10,046th since this became a proper blog in 2005.
The corrected data doesn't meaningfully change the overall statistics. I post 1.36 times per day on average, with a mean of 41.34 and a median of 42 posts per month (standard deviation, 7.868). The maximum for a month remains 60 (November 2008) and the minimum is still 15 (October 2007).
At my current rate of posting (38.42 times per month in 2025), I should reach 15,000 posts in May 2036 and 20,000 posts in March 2047. Stay tuned!
-
I did promise to revise my conclusions once I identified the real 10,000th post.↩
Yesterday morning, Immigration and Customs Enforcement—who have no jurisdiction over US citizens—murdered another US citizen in what witness videos clearly show as a depraved act involving at least two shooters. Alex Pretti, the murdered ICU nurse who tried to shield other observers from being assaulted with chemical irritants, was unarmed and subdued when ICE agents shot him at least 8 times.
This morning, a Federal judge in Minneapolis ordered ICE not to destroy or alter the evidence they've collected about the murder, because even the dimmest bulb in the ICE marquee knows they had no justification for this.
I'm not going to link to the videos; they're not hard to find. You should watch them, though, from at least two angles. If you don't believe there is probable cause to charge at least two of the ICE agents with at least 2nd-degree murder, please find the nearest inpatient facility and tell them you're a psychopath.
ICE claimed that Pretti had a gun and planned to shoot the agents. The videos clearly show he made no aggressive moves toward the agents and was in fact trying to remove himself and another victim of ICE violence from the scene. And, of course, until recently the same people yelling "he had a gun!" are exactly the same people who pushed so hard for an extremist interpretation of the 2nd Amendment that allowed Pretti to carry his pistol completely legally. As much as I think we should not have average citizens carrying pistols in cities like Minneapolis, Pretti didn't deserve to die.
And as much as the "2A" fanatics raved about carrying guns to the grocery store was necessary to prevent the government from trampling our rights, I ask them, what the fuck do you think happened yesterday? It's funny how they seem to have forgotten that squishy little diarrhea blossom Kyle Rittenhouse.
Speaking of the 2nd Amendment, Tim Walz needs to remember why we have that amendment, and use the state's well-regulated militia to protect Minnesotans from further violence.
Josh Marshall warns that OAFPOTUS administration officials want to escalate the violence to dominate the area:
Escalation dominance” is a concept in military theory and strategy. Imagine you have two countries in a tit-for-tat confrontation. The country with escalation dominance has superior capabilities on every rung up the so-called escalation ladder. So at every stage that country has the upper hand. It has more and better guns. So every escalation puts the weaker country in greater danger and with less hope of ever getting the upper hand. The weaker power faces the bad choice of either backing down or incurring ever greater injury and ultimately destruction.
Why would the White House continue to escalate in the face of rising public opposition? One answer is that they’re fanatics and true believers. But a complementary explanation is this belief in escalation dominance. It may not be popular but they believe public resisters will eventually have to knuckle under. So they’re happy to keep escalating. Because they have more and bigger guns and eventually those who oppose them will have to give in. I don’t think that’s the case. But I’m pretty sure they do.
My party's top officials, who haven't yet figured out that the Republican Party left the land of the sane 32 years ago, made the usual noises and press releases. (Senator Schumer, just fucking retire already.)
This has to stop. It will stop. But clearly, the OAFPOTUS and his droogs will continue to escalate, as their unconstitutional and dangerous1 secret May memo made clear. Like all authoritarians, neither the OAFPOTUS, nor Reichsführer-ICE Stephen Miller, nor CBP chief Greg Bovino2 don't care who dies, as long as they "win." But like all authoritarians, their own psychopathy prevents them from understanding a basic truth: empathy makes collective action more effective. And there are way more of us than there are of them.
-
By encouraging ICE agents to illegally enter people's homes without an Article III warrant, it seems like Miller et al. want one of them to get shot as an excuse to rachet up the militarization of the operation. It's a tried-and-true technique of authoritarians everywhere.↩
-
Someone said "Bovino looks like an aging lesbian" and I can't unsee it.↩
The temperature at Inner Drive Technology World HQ dropped below freezing at 8:52 pm last Friday and will probably not go above freezing until at least February 6th. We have had three-week stretches below freezing many times, and every one of them has sucked. I lived through the longest below-freezing stretch in Chicago history, the 43 days between 28 December 1976 and 8 February 1977. I also lived through the record low of -33°C (-27°F) on 20 January 1985, the earliest first freeze on 22 September 1995, and the latest freeze on 25 May 1992.
At least the forecast predicts it'll get above -17°C (0°F) by noon. The temperature bottomed out at -20.8°C (-5.4°F) at dawn but it's already 2.4°C (4.3°F) warmer two hours later. If we get to the forecast high of -13°C (9°F), Cassie will be able to stay outside for 10 whole minutes, if she wants to.
I have to remind myself that we stay in this part of the country in part because this weather sucks to biting insects way more than it sucks to large mammals with central heating. Also, it Builds Character™.
Like so much in the world, we had ample warning that things would not go well. Seven weeks ago I noted that the La Niña phase had started to collapse, and that while La Niña correlates with cold winters here, the transition to ESNO-neutral wouldn't happen in time to save us from...this.
It warmed up, sort of
CassieChicagoElection 2026Fitness devicesHealthPoliticsTrumpWinterWorld Politics
After bottoming out at -21.3°C (-6.3°F) around 8:30 this morning, the temperature has skyrocketed to -18.7°C (-1.7°F) a few minutes ago. I decided to walk to my optometrist appointment, 12 minutes there and 13 minutes back thanks to a red light, which wasn't too bad in my swaddling. When I got back, Cassie lasted just over 4 minutes before bolting for my front door. Smart dog.
Outside Chicago, things look a lot worse: a major winter storm has formed west of Texas with a trajectory that will hit just about every population center from Albuquerque to Boston over the next 72 hours—except us. Even Louisiana Governor Jeff Landry had to warn his constituents to "get off the roads, get comfortable, and cook a gumbo." (My dinner tonight will be homemade chicken soup, but same principle.)
In other news:
- Tom Nichols dreads finding out how the US military will react to truly unhinged orders that could come from the OAFPOTUS. Julia Ioffe concurs.
- Matthew Yglesias looks at the collapse of childhood vaccinations and wonders if we'll be able to fix this horrible legacy.
- Jeff Maurer tries to make sense of a new poll showing a plurality of voters calling themselves "independent" but don't seem to want a new, centrist party. That said, "to some extent, Gallup’s question doesn’t measure how much people identify with either party, but rather how cool it is to call yourself 'independent.'"
Finally, fitness technology company Strava is going public, a move that The Economist thinks is cause for a below-average dad joke.
The temperature at Inner Drive World HQ has slid down to -20.9°C (-5.6°F), the coldest temperature we've had in two years. O'Hare shows -23.9°C (-11°F), which is colder than the low temperature in January 2024; the last day it got this cold was 31 January 2019, when it hit -29.4°C (-21°F).
Most of the schools in the area have closed for the day, Metra has a reduced schedule (not that anyone is riding the trains today), and Cassie did not feel any need to sniff every blade of snow-covered grass before doing her business this morning.
No danger of a record low, however. On 23 January 1963, it was -27.8°C (-18°F). That said, if the temperature doesn't go above -19°C by midnight Sunday, we'll set the record for the coldest high temperature.
I can't wait for my eye doctor appointment at lunchtime. Hey, it's only a 15-minute walk, right?
In my last post on how the Daily Parker blog engine works, I talked about the fundamental abstractions that I built it around. Today I'm going to talk about the code some more, but more concretely, by explaining how the application decides who can see or do what. I'm a little proud of this design, to be honest.
Just a quick reminder of the difference between authentication and authorization: authentication confirms that you are who you say you are; authorization decides what you can do. The Daily Parker lets Microsoft handle authentication and just trusts that they're doing it correctly. (I'm planning to add other authentication services, including Google and Facebook.)
So assuming that a user is who she claims to be, what does the blog engine do with that information?
When someone attempts to do something that requires a permission, the app first asks the security middleware for the person's user ID, then uses that ID to read the person's profile, which is stored in the app's database. The profile contains a list of the user's roles and the privileges they have within each role. Role names are arbitrary; I can define them as I need them without changing the software. So far I've defined 9 roles, including "Blog post" and "Comment," which are the two visitors interact with the most even if they don't know they do. Each role has five possible privileges: List, Read, Change, Delete, and Self. For example, to write a blog entry like I'm doing now, a user has to have the Blog Post role with Change privilege. (Of course, most of the app's basic functions work fine if you don't bother authenticating. Anonymous users account for over 99% of the blog's page views, after all. But even anonymous users need to be authorized to do stuff. The application still checks authorizations at every step,)
In some cases, a user just has to be in a particular role to see certain information. For example, to see the "add blog post" icon on the navigation bar, you have to have the Blog Post role. The Blazor middleware enforces that with AuthorizeView containers.
Once you're on a page, though, authorization may get more finely-tuned. The view blog post page (on which you're probably reading this right now) makes five specific checks before revealing things like the edit button and the post metadata footer. Here's where we get to the code I'm pretty jazzed about.
At the top of the authorization chain is a call to IAuthorizationService.IsAuthorizedAsync, which simply returns true or false. It looks like this:
Task<bool> IsAuthorizedAsync(
Project? project,
UserProfile? user,
IAuthorizable? item,
string feature,
Privileges demand,
CancellationToken cancellationToken = default);
(The Async keyword and suffix just means that the code runs on its own thread so it doesn't block the rest of the application from running. Lack of async code caused most of the performance problems with the BlogEngine.NET version of this application, so it was important for me to build the entire app around asynchronous code blocks.)
The project, user, item that you want to use, role that you need to have, and privileges you require to use it comprise an AuthorizationState, which is used by this method:
public async Task<bool> IsAuthorizedAsync(
AuthorizationState state,
bool logResult = false,
CancellationToken cancellationToken = default)
{
var allowed = false; // If no strategy applies, deny by default
var strategyName = "no strategy";
var userName = state.User?.Id ?? "(anonymous)";
var strategies = state.Item is null
? DefaultAuthorizationStrategies
: DefaultAuthorizationStrategies.Union(state.Item.AuthorizationStrategies); // General, then specific
foreach (var strategy in strategies)
{
var result = strategy(state);
switch (result)
{
case AuthorizationResult.Allow:
allowed = true;
break;
case AuthorizationResult.Deny:
allowed = false;
break;
case AuthorizationResult.None:
default:
continue;
}
strategyName = strategy.Method.Name.Humanize();
if (!allowed) break; // Any explicit Deny takes precedence
}
StrategyUsed = strategyName;
if (!logResult) return allowed;
var description = string.Concat(state.Description, " (", strategyName, ")").Trim();
if (allowed)
{
await actionLog.WriteAsync(state.Feature, state.Demand.ToString(), userName, ActionLogResult.Authorized,
state.Item?.Id, description, cancellationToken).ConfigureAwait(false);
logger.LogDebug("{User} authorized to {Demand} {Feature} on {Type} {Item} using {Strategy}",
userName, state.Demand, state.Feature, state.Item?.GetType().Name, state.Item?.Id, strategyName);
}
else
{
await actionLog.WriteAsync(state.Feature, state.Demand.ToString(), userName, ActionLogResult.Unauthorized,
state.Item?.Id, description, cancellationToken).ConfigureAwait(false);
logger.LogInformation("{User} not authorized to {Demand} {Feature} on {Type} {Item} using {Strategy}",
userName, state.Demand, state.Feature, state.Item?.GetType().Name, state.Item?.Id, strategyName);
}
return allowed;
}
Have you seen the clever bit? It's on the 4th line (beginning with var strategies =). You see, every type of item that requires authorization implements an interface called IAuthorizable that has this member:
Func<AuthorizationState, AuthorizationResult>[] AuthorizationStrategies { get; }
That's a bit of functional programming hiding out inside an object-oriented interface. It allows the objects themselves to decide how they authorize actions based on their own internal state. Each item in a class's AuthorizationStrategies collection is a function that takes an AuthorizationState and returns an AuthorizationResult which is either Allow, Deny, or None. Allow means "the action is authorized," deny means "the action is prohibited," and none means "it's not my place to decide." As you can see in the IsAuthorizedAsync code, though, actions must have an explicit Allow result to be authorized. Once an action is denied, the discussion ends; "allow" and "none" are always provisional until all of the applicable authorization strategies is checked.
For example, here's the BlogPost.FuturePost method, which is one of the checks that occurs nearly every time someone tries to read a blog post:
private static AuthorizationResult FuturePost(AuthorizationState state)
{
if (state.Item is not BlogPost post
|| state.Project is null
|| post.Start <= DateTimeOffset.UtcNow) return AuthorizationResult.None;
if (state.User is null) return AuthorizationResult.Deny;
var user = state.User.Id;
if (post.Owner == user) return AuthorizationResult.Allow;
if (state.Project.Users.Contains(user)) return AuthorizationResult.Allow;
return AuthorizationResult.Deny;
}
First, the method makes sure that the item is a blog post, that it has a project associated with it, and if it's a blog post, that its start (post) time is in the future. If the answer to any of those questions is "no," the method returns None, because it's not up to the BlogPost class to determine what to do.
Next, if there is no user—i.e., it's an anonymous request—the request is denied. This ensures that you have to be logged in to see a future post.
But we're not done, because the next three lines require either that the person requesting to see the post is the one who created it (the owner), or if not, that the person is a member of the project associated with the post. If either of those things is true, the request is tentatively allowed. If neither is true, it's denied.
Why tentatively? Remember that an "allow" result is provisional. Before the class-specific authorization strategies even start, the authorization service runs its own checks in this order:
- Is the authorization state itself valid?
- Was the user deleted?
- Does the user have the requested privilege? (Sure, you're a member of the project, but you don't have
BlogPost/Readprivileges, so...nope.) - If the request is to change or delete something, is the user a member of the project?
- Is the request just to list something that only requires authentication to list? (This solves a specific problem with anonymous users that wasn't immediately obvious to me.)
- Is the user requesting authorization the owner of the item?
- Is the item open for public reading? (This is the one that lets you, dear anonymous visitor, read this post.)
- Is the item itself deleted?
Only if every one of those checks and the item's own checks ends with "Allow" does IsAuthenticatedAsync return Allow.
And because the individual classes have their own authorization strategies, I don't have to change any of the authorization code when I create new things for the project. The authorization service doesn't care what the item it's authorizing is, as long as it implements the IAuthorizable interface. So if I create a new FuelRecord class for keeping track of when I fill up my car, the FuelRecord can decide for itself who can use it, and I don't have to change any other lines of code.
By the way, there are about 150 unit tests around this, including dozens of checks against all five privilege types for each authorization state I could think of. It's tedious, but like the Inner Drive Money class, it's something I want very much not to screw up.
I mentioned in a post weeks ago that I've been thinking about this software for 10 years. This was the second-hardest problem to solve. I think I came up with a pretty cool solution. Let me know what you think in the comments.
The longest cold snap in years is right now descending upon us from the northwest. It's still a tolerable -5°C at Inner Drive Technology WHQ, but this forecast, man... It looks like temperatures will dip below -17°C (0°F) around 2am tonight and stay there until 7am Saturday, bottoming out around -22°C (-7°F) right before dawn tomorrow.
Cassie has a double coat and paw beans of steel, but she's not a husky, nor does she have great judgment about how cold she feels. She also completely fails to predict the future farther than about 30 seconds in advance. So as a rule, I limit her outside time based on the temperature. Above -5°C she can stay out as long as she likes; at -10°C it's 15 minutes, declining to 3 minutes at -18°C or below. So it's possible she will only get 12 minutes of outside time tomorrow. Have you ever seen a Weimaraner mix on only 12 minutes of walkies? Yeek.
Somehow I'll get stuff done tomorrow and Saturday, including an eye exam at lunch time. Ordinarily I walk about 15 minutes to the optometrist, but tomorrow I think I'll drive. Can't wait.
I will get to the next "how this works" posts soon
CassieChicagoEntertainmentEuropeFoodIllinoisPoliticsTrumpUS PoliticsWinterWorkWorld Politics
I've just had a lot to do today and I'm not feeling particularly creative. So, nu, maybe Friday?
Meanwhile:
- The Secretary General of the Council of Europe, Alain Berset, wonders WTF is going on in what's left of the OAFPOTUS's brain.
- A bunch of convicted (but pardoned) violent criminals could get some of my tax money handed to them by the OAFPOTUS's droogs. Remember: accepting a pardon means the person has admitted guilt for the crime.
- Amanda Nelson has some practical advice about how not to lose your mind during this time of infantile, demented chaos.
- The Chicago City Council just voted to exempt THC drinks from the unregulated hemp ban that takes effect April 1st. Delta-8, -9, and -10 products will still be banned.
- Chicago has 26 semifinalist nominees for the James Beard Awards this year.
Finally, despite the temperature having risen to the January 21st normal of -1°C this afternoon, just look at this graphical forecast for the 48 hours starting at midnight tonight:
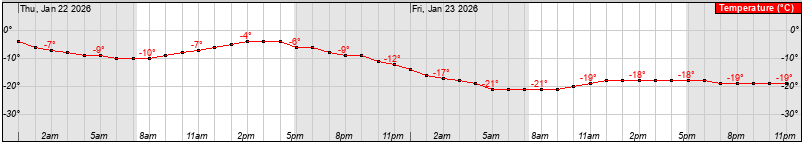
Wonderful. Looks like a solid 28 hours below -17°C (0°F) before "warming up" to -11°C (12°F) late Saturday. And poor Cassie has only gotten 4½ hours of walkies in the last 7 days. Even the 10-day forecast has us below freezing as far as it can predict.
We last had a temperature of -21°C (-6°F) two years ago, and wow, I didn't like it at all when I got off the plane from Seattle. I can hardly wait to bundle up and hunker down Friday. Yay.
I just released a new production version of the Inner Drive Journal (the software the Daily Parker runs on) with 7 bug fixes, 9 new stories, and a technical task. Most of these Jira cases took me less than 15 minutes. Yesterday, though, I wound up spending 5 hours on a new system configuration management tool because (a) it's complex and (b) I changed my mind about the interface after I ran it a couple of times.
The coolest new feature is the Calendar, which allows you to view whatever was posted on a particular date. That's...well, that's the only feature that anonymous users can see. (So create an account already!)
The same with the bug fixes; for now, I'm the only one who will notice them, because I'm 100% dogfooding. For example, the Edit Blog Post page has an auto-save feature: every n seconds (which is now configurable by project), it saves what you're working on as a draft. Once the post is published, though, the feature turns itself off. You can control whether it's on or not at any time using a checkbox on the Edit page.
That's a super-useful feature, solving one of my biggest irritations with BlogEngine.NET. We can all agree it's no fun losing a draft you've worked half an hour writing. However, as I first implemented the auto-save feature, it simply called the general Save method on the page, which happily tells you about its every success with a banner at the top of the page. This causes everything to shift briefly and can cause the editing box to lose focus, which interrupts the writing flow. I fixed it by only showing the "success" banner when you actively click the Save button, but not when it auto-saves. I'm now 10 minutes into writing this post and, yes, it's a lovely improvement.
Unfortunately, a couple of the new features work in the dev/test environment but not in production (timing issues, I'm pretty sure), and I got the logic wrong in a couple of places. I'll fix those quickly and probably have a new release on Sunday or Monday. I'm also going to start working on some of the more journal-like features, starting with new layers of privacy, and possibly some external interactions I've wanted to do for years. We'll see. Plus, I'm starting to see some opportunities for better app performance, though I am really very happy by how it's running—especially compared with its predecessor.
And, yes, I'll have another How This Works explainer up as soon as I can.
One year of weaponized dementia
CrimeEconomicsElection 2026HealthHistoryLawPsychologyRepublican PartyTrumpUS Politics
Exactly one year ago this hour, the worst administration in American history took office. One hopes they will always be the worst administration in history (though I can see some ways that becomes true for some pretty horrible reasons).
In the past year, as the OAFPOTUS has descended deeper into dementia and his existing malignant narcissism, his droogs have torn down the domestic and international structures that provided the longest period of prosperity in history. Not everyone is horrified, of course; the OAFPOTUS has done Vladimir Putin's work so effectively the Russian dictator openly gloats about it.
Will we have three more years of this, or will the Republicans in Congress and in the Cabinet who keep him there end the nightmare sooner?
Even the people who believe in their tiny, cold hearts that destroying the welfare state is the only way we can have a prosperous billionaire class (looking at you, Russell Vought), or you believe that getting rid of every immigrant who arrived after 1830 will make up for you not getting to sit with the cool kids in 2nd grade (looking at you, Stephen Miller), aren't you tired of the chaos?
I should note, today is also the anniversary of the Wannsee Conference, when Stephen Miller's boyhood crush Reinhard Heydrich and his pals planned the murder of 11 million Jews in Europe. That was only 9 years after the National Socialists took power in a (mostly) democratic election. We're living through history repeating as farce, to be sure; but Miller has built concentration camps while the OAFPOTUS celebrates brownshirts killing moms in Minneapolis.
Elections for the 120th Congress take place in just 287 days. Everything points to an overwhelming swing towards the Democrats. Taking back Congress will slow but not stop the mayhem, unless the Republican Party decides they decide to take action with us. We'll see; so far, they seem to want everything to burn down so they can rule the ashes.
Woe to thee, O land, when thy king is a child, and thy princes eat in the morning.—Ecclesiastes 10:16
Copyright ©2026 Inner Drive Technology. Donate!